Graph Based Concurrency Control Protocol in DBMS
Last Updated : 05 Feb, 2025
In a Database Management System (DBMS), multiple transactions often run at the same time, which can lead to conflicts when they access the same data. Graph-Based Concurrency Control Protocol helps manage these conflicts and ensures that the database remains consistent.
- In this protocol, transactions are represented as nodes in a graph, and conflicts between them are shown as edges.
- Before granting a lock on a data item, the system checks for cycles in the graph. If a cycle is detected, one of the transactions is rolled back to prevent deadlock and ensure smooth execution.
- A Graph-Based Protocol is a way of implementing Lock Based Protocols. It is deadlock free, but no guarantee of recoverability.
This method is more powerful than traditional locking techniques, as it can handle complex dependencies between transactions. However, it can be computationally expensive for large databases.
A prerequisite of this protocol is that we know the order to access a Database Item. For this, we implement a Partial Ordering on a set of the Database Items (D) {d1, d2, d3, ....., dn} . The protocol following the implementation of Partial Ordering is stated as-
- If di --> dj then any transaction accessing both di and dj must access di before accessing dj.
- Implies that the set D may now be viewed as a directed acyclic graph (DAG), called a database graph.
Tree Based Protocols is a simple implementation of Graph Based Protocol.
Tree Based Protocol
The Tree Protocol is a graph-based concurrency control method that ensures conflict serializability and deadlock freedom. Unlike Two-Phase Locking (2PL), it follows a hierarchical structure for locking data items.
Rules of Tree Protocol
- Only exclusive (X) locks are allowed – No shared (S) locks are used.
- The first lock can be on any data item – After that, a transaction can lock a data item only if it has locked its parent first.
- Data items can be unlocked at any time – There is no strict two-phase rule.
- No relocking – Once a transaction unlocks a data item, it cannot lock it again.
The Tree Protocol offers a balance between concurrency and deadlock prevention, making it useful in certain database applications.
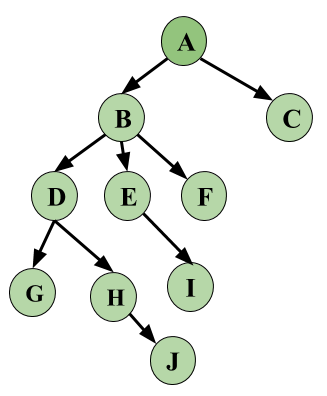
Image - Database Graph
Let's look at an example based on the above Database Graph. We have three Transactions in this schedule and this is a skeleton example, i.e, we will only see how Locking and Unlocking work, let's keep this simple and not make this complex by adding operations on data.
| | T1 | T2 | T3 |
|---|
| 1 | Lock-X(A) | | |
|---|
| 2 | Lock-X(B) | | |
|---|
| 3 | | Lock-X(D) | |
|---|
| 4 | | Lock-X(H) | |
|---|
| 5 | | Unlock-X(D) | |
|---|
| 6 | Lock-X(E) | | |
|---|
| 7 | Lock-X(D) | | |
|---|
| 8 | Unlock-X(B) | | |
|---|
| 9 | Unlock-X(E) | | |
|---|
| 10 | | | Lock-X(B) |
|---|
| 11 | | | Lock-X(E) |
|---|
| 12 | | Unlock-X(H) | |
|---|
| 13 | Lock-X(B) | | |
|---|
| 14 | Lock-X(G) | | |
|---|
| 15 | Unlock-X(D) | | |
|---|
| 16 | | | Unlock-X(E) |
|---|
| 17 | | | Unlock-X(B) |
|---|
| 18 | Unlock-X(G) | | |
|---|
From the above example, first see that the schedule is Conflict Serializable. Serializability for Locks can be written as T2 --> T1 --> T3.
Data items Locked and Unlocked are following the same rule as given above and follow the Database Graph.
Advantages of Tree Protocol
- Deadlock-free – No cycles form in the lock order, so no rollbacks are needed.
- Increased concurrency – Unlocking can happen earlier than in Two-Phase Locking, reducing wait times.
- Allows different schedules – Some schedules that are not possible under 2PL can be executed under the tree protocol.
Drawbacks of Tree Protocol
- No guarantee of recoverability – Can lead to cascading rollbacks if not handled properly.
- Extra locks required – Transactions may need to lock unnecessary data items, increasing waiting time and locking overhead.
- Some schedules allowed in 2PL are not possible in Tree Protocol – While it provides flexibility, it also has limitations.
FAQs on Graph-Based Concurrency Control Protocol in DBMS
What is Graph-Based Concurrency Control in DBMS?
Graph-Based Concurrency Control is a method that represents transactions as nodes in a directed graph, with edges showing conflicts when transactions access the same data. It ensures consistency by detecting cycles and resolving conflicts.
How does the Graph-Based Concurrency Control Protocol prevent deadlocks?
It prevents deadlocks by ensuring that transactions follow a predefined partial order when accessing data items, forming a Directed Acyclic Graph (DAG). If a cycle is detected, a transaction is rolled back to maintain serializability.
What is the role of partial ordering in Graph-Based Concurrency Control?
A partial order is imposed on data items, meaning if a transaction accesses a set of items, it must access them in a specific order. This ensures a structured execution pattern and prevents cyclic dependencies.
How does the Tree Protocol relate to Graph-Based Concurrency Control?
The Tree Protocol is a type of graph-based concurrency control where transactions acquire exclusive locks following a hierarchical structure. This prevents deadlocks but may require transactions to lock unused data, increasing overhead.
What are the advantages and limitations of Graph-Based Concurrency Control?
It efficiently manages complex dependencies and eliminates deadlocks but can be computationally expensive and less scalable for large databases with many concurrent transactions. The need for predefined ordering can also reduce flexibility.